Tesla app is insecure by design. This is what Elon Musk can do to change it
Tesla has become synonymous for a new trend in the automotive industry. Elon Musk’s electric car is on the lips of the whole world – or even the whole solar system after SpaceX shot it into space. That’s why it’s so shocking that a more “earthly” matter – the security of Tesla software – is far below modern standards.

Table of contents
Tesla is not only a symbol of the new “electrification” of the car market but also one of the most distinct examples of how the Internet of Things (IoT) is becoming part of our everyday life. In the IT sector there is a popular saying that:
The S in IoT stands for security
which perfectly reflects the problem of the Internet of Things resulting from poor security standards. We were curious whether the same problems might be present in the case of an IoT car.
There are a lot of Tesla fans at Boldare, and since our Co-CEO Piotr Majchrzak’s Tesla Model X is parked just in front of our office, we’ve decided to check it out in a little more depth.
Is Tesla App Safe to Use?
The Tesla’s mobile app is a remote car control center for users. It allows checking information such as battery level or vehicle location. It can also operate the air conditioning, honk the horn, open the trunk, or even unlock and start the car. It might seem that with options like these available, the app should be as secure as Fort Knox.
Far from it! The gateway to a Tesla car worth tens of thousands of dollars is secured by merely a password. You just need a password and you could steal the car and drive away. Or even possibly worse – an unauthorized person could use the app to track the car without the owner’s knowledge.
During our tests, we identified some key problems with security. We found that the real security problem isn’t incorrect implementation but actually, the security assumptions adopted during the design and development of the Tesla app and website. This can have serious consequences related to the third-party app ecosystem.
So, what’s missing from the Tesla app, and what features should it have from a security perspective?
Tesla App Security Issues
Multi-Factor Authentication
Nowadays, a single password is considered insufficient, being a typical case of a Single Point of Failure. To prevent unauthorized access to all kinds of IT systems, multi-factor authentication (MFA), also known as two-factor authentication (2FA), is commonly used. You will come upon MFA everywhere: e.g., when you want to withdraw money from an ATM or pay for something, you need to have the card and also know the PIN code.
If you want your e-mail account to be safer, you can turn on 2FA in form of SMS codes or a dedicated app. This is actually standard these days, in everyday use by companies such as Google, Facebook, Microsoft, Apple, and Dropbox. Which makes Tesla’s attitude even more surprising.
No form of MFA is available in Tesla app, not even as an optional functionality. What does this mean? Once again, it means that by obtaining just one password, you can gain full control of the car. It’s rather peculiar that you can secure your email inbox with 2FA but you can’t do the same for an app that controls an expensive edge-tech car.
And it’s not only the mobile app that lacks MFA. Access to the account via the official website doesn’t require or offer any additional security layer, too. You just need the same password that is used for the application. Even though it is not possible to control the car through the website, the personal user account contains sensitive data such as invoicing and credit info.
New device verification
We expected that if 2FA isn’t being used in its typical form, at the very least new devices would need to be verified. How might that work? Take a look at this example.
If you want to log in to your Steam account on a new computer, you must authorize the new device first. Otherwise, you simply won’t be able to use your account.
Steam - Authentication of new device:

Additionally, you will get an email informing you about the log-in attempt via a new device, containing the IP address of the device. Simple, comfy, and safe.
If you have the login and password to a Tesla Account, that’s enough to log in to the app on a new smartphone and gain full control of the car. Tesla doesn’t care about the number of devices synced with your account. Nor will you be informed that someone has logged in to your account from another device.
This problem could be solved by introducing a new device confirmation feature to the Tesla Account. It wouldn’t really affect the ease and comfort of using the app (after all, how often do you buy a new smartphone?) but it could considerably increase user control over the account and its security. It actually surprised us that this solution is not available in any form for the Tesla app or on the website.
What’s more, the app should ideally contain a section enabling a user to manage the verified devices synchronized with the Tesla Account. If it did, the user would be aware of which devices are logged in and could control their access.
We prepared a design mockup presenting how it could look like:
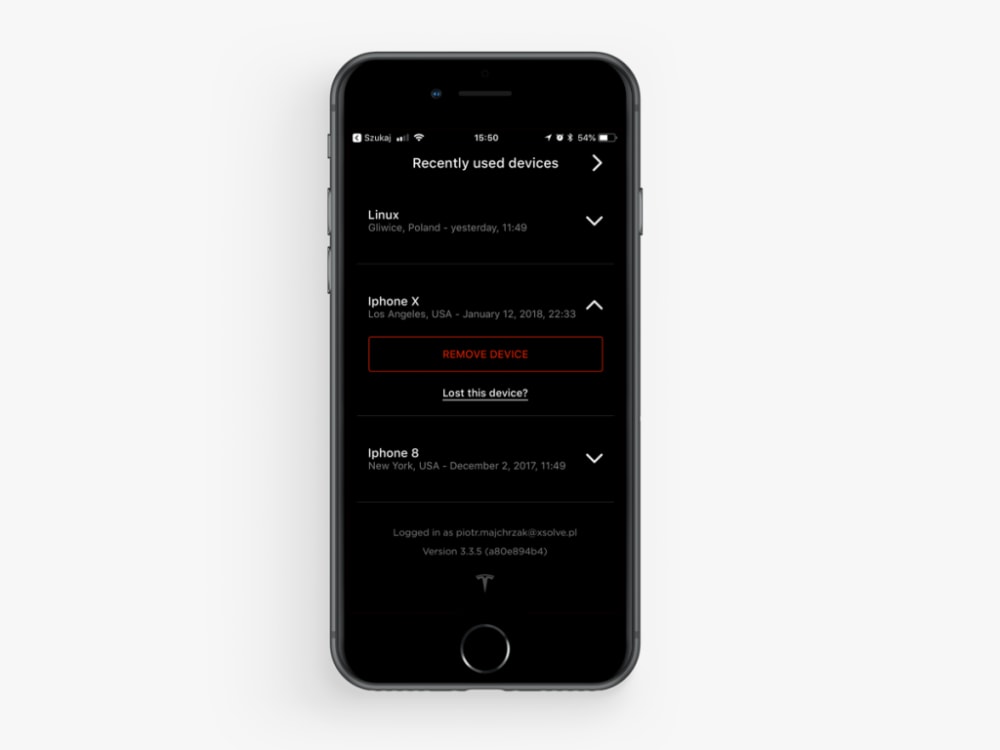
Non-standard user activity detection
We thought that Tesla might have decided to employ some form of user activity classification and, for instance, deny access if abnormal activity is detected.
During our tests, we logged in to the same account using multiple different devices at the same time. We were able to do it even if the car was hundreds of miles away. We could use the the full range of app functionalities without any trouble and, from an owner’s perspective, we didn’t trigger any security alerts.
We can’t be hundred percent sure in this case but based on our usage of the application, we can assume that non-standard activity detection is not implemented or at least it’s not working as you might hope it would.
Insufficient notification system
Even though the Tesla app offers a system of notifications, these only support standard user activity, for example, charging-related notifications. The only ones that can be classified as “security” notifications are Car Alarm and Software Update. Let’s be honest, this isn’t enough.
Taking into account all the flaws of the app mentioned above, there should be notifications related to safety, including logging in on a new device, turning mobile access on and off, or switching the valet mode. These few simple measures would enhance users’ security and prevent other persons from taking control without permission.
How these notifications could look like? Check this design mockup:

The lack of notifications is also painfully obvious on the website. Usually, when you change the password to an account, you receive an email with a confirmation link to follow, or at least a notification informing you that your password has been changed. Not in Tesla’s case. Changing the password consists of providing the old password, entering the new one, et voilà! As a user, you’re not even informed about the change of password, neither by email nor by text message.

A dangerous ecosystem
Tesla does not officially share an API enabling communication from external applications. However, in practice, the API used by the official app has been quite well-documented by the community and is currently in wide use among users – mostly through external, non-official apps.
Users probably use these apps because they offer functionalities which are not available from Tesla officially. Tesla holds no responsibility for external apps but at the same time, it has an ability to exert an influence on how the ecosystem looks and operates.
No Safe Authentication Opportunity
Another problem lies in the lack of safe authentication method and permissions management. The apps make use of the only method available: users’ credentials. This, in turn, practically deprives users of any control over them and makes it possible for an unauthorized person to gain full control of the car.
Here’s one of the applications using user credentials - TeslaSpy.com:
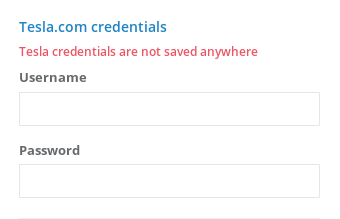
To be perfectly clear, it is not our intention implying that a specific service or product is insecure in any way. This is just an example.
Security-conscious users aren’t likely to share their system login data with an unknown external app, but those who are less aware might do so.
What can Tesla do in this situation? The company could choose to influence the ecosystem and encourage its development in a more secure direction. At least two mechanisms could be used to do so.
API Keys
One of the options is to allow API key generation, which could be utilized by users in external apps. Combining that with permissions control, users would be able to use external apps while giving them access to particular rights only (e.g. getting information without permissions to perform any actions). However, API keys might not be user-friendly enough for normal use.
OAuth 2.0 – “Tesla Sign-In”
Instead of typical API keys, it could be more convenient to use OAuth 2.0, just like in for example Google Sign-In or Slack Sign-In services. This way, a user could log in to the Tesla website safely and then see what kind of access the app expects and let it access the Tesla Account with specific permissions only. This would be also useful if the user could control the authorized apps later on.
This is how it can look:

Making Tesla app more secure
In the 21st century, the question of software security is one of the hottest subjects. The Facebook – Cambridge Analytica data scandal has shown that it is not acceptable to treat users’ privacy and data security carelessly. Apps using personal data should meet the strictest security standards.
Sadly, the Tesla app and website are at a very low security level when it comes to protecting sensitive data. Not due to technical vulnerabilities but instead resulting from the app’s basic security principles. The lack of MFA or authorization control for new devices in the case of a product which gives access to a car plus the ability to track its location is terrible negligence – to put it mildly.
Boldare doesn’t specialize in security, but we definitely know how to create top-quality software. And you can’t talk about quality without thinking about safety. Ease of use and software security must go hand in hand; they are not mutually exclusive and require a careful balance. Tesla, unfortunately, gives the impression that they forgot about the “security” issue, at least in some areas.
And finally, a few words from Boldare’s Co-CEO:
Dear Mr. Elon Musk, we would be pleased to write an app for you which will both enable users to manage their Tesla cars easily and better ensure their security and privacy. And as we are fans of Tesla and your other initiatives, we’ll even do it for free.
Share this article:








